Bash prompt variables
These are the variable substitutions used above.
\u user \h hostname \w ~/path/to/directory
These are the variable substitutions used above.
\u user \h hostname \w ~/path/to/directory
About Environment Variables
Environment variables are specially named aliases for basic system properties. Here is the Microsoft definition:
Environment variables are strings that contain information such as drive, path, or file name. They control the behavior of various programs. For example, the TEMP environment variable specifies the location in which programs place temporary files.
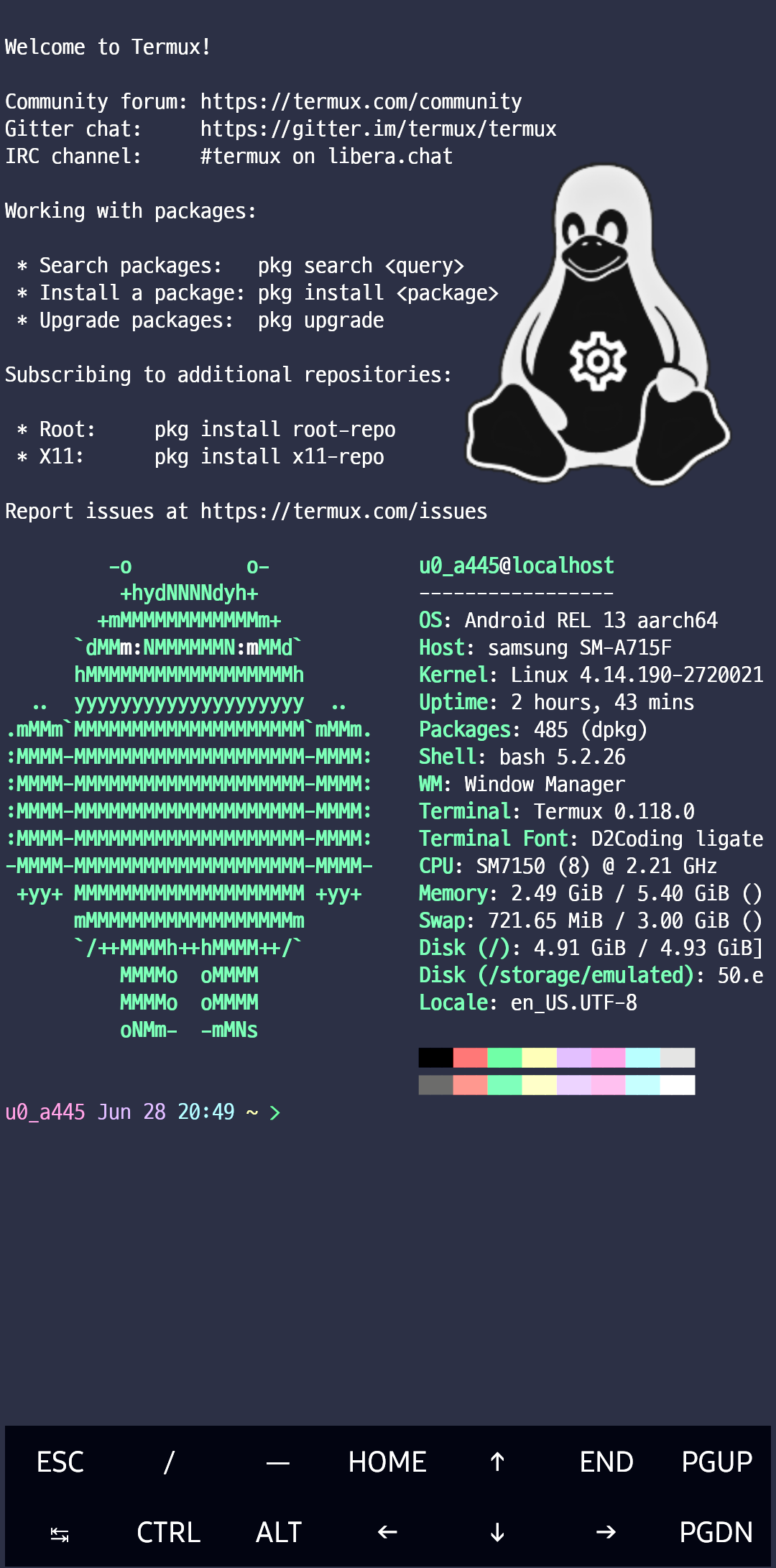
Introduction
In today’s world, mobile devices have evolved from mere communication tools into powerful computing platforms. A key player in this transformation is Termux, an application for Android devices that offers a comprehensive terminal emulator and Linux environment. In this article, we will explore what Termux is, why you should use it, and its fundamental features.
What is Termux?
Termux is an application for Android operating systems that functions as a Linux-based terminal emulator and command-line interface. It offers users a near-complete Linux experience with advanced features and a broad package repository, making it suitable for programming, file management, network analysis, and more.
Why Should You Use Termux?
There are several reasons to choose Termux:
Mobile Freedom: Termux transforms your Android device into a full-fledged computing tool. You can work in a Linux-based environment wherever you are.
Learning and Development: It’s an excellent learning tool for students and developers. Termux facilitates gaining experience in various programming languages and tools.
Security Research: For IT professionals and security researchers, Termux is a valuable tool for fieldwork.
Customizability and Extensibility: Termux can be customized to meet user needs and expanded with various plugins.
Key Features of Termux
Linux Terminal Experience: Supports popular shells like Bash and Zsh.
Comprehensive Package Management: Install many Linux packages using apt or pkg.
Development Tools: Allows development in languages like Python, Ruby, Node.js.
SSH Access: Functions as both an SSH client and a server.
File Editing and Management: Edit files using editors like Vim and Nano.
Conclusion
Termux is a Linux-based terminal emulator for Android devices, transforming them into powerful computing and development tools. Suitable for both learning and professional use, this application offers flexibility and powerful functionality on mobile devices. Termux is an ideal tool for technology enthusiasts, developers, and IT professionals, allowing you to push the limits and experience a full Linux environment on your mobile device.
Special commands to sqlite3 (dot-commands)
Most of the time, sqlite3 just reads lines of input and passes them on to the SQLite library for execution. But input lines that begin with a dot (“.”) are intercepted and interpreted by the sqlite3 program itself. These “dot commands” are typically used to change the output format of queries, or to execute certain prepackaged query statements. There were originally just a few dot commands, but over the years many new features have accumulated so that today there are over 60.
For a listing of the available dot commands, you can enter “.help” with no arguments. Or enter “.help TOPIC” for detailed information about TOPIC. The list of available dot-commands follows:
(more…)
Some basic linux:
uname -a
uname-r
uptime
hostname
hostname -i
last reboot
date
cal
W
whoami
finger user
Default etc/ssh/sshd_config file for ssh:
(more…)
Danas gotovo sve web stranice u sebi sadrže JavaScript. To je programski jezik, koji se izvršava u web pregledniku. On web stranicama osigurava određene funkcionalnosti i ako je on iz nekog razloga onemogućen, može se dogoditi da određeni sadržaj ili njihova funkcionalnost bude ograničena ili nedostupna. Na ovoj stranici nalaze se upute kako uključiti (omogućiti) JavaScript u pet najčešće korištenih web preglednika.
Android Permissions – Protection Levels
Android applications declare the permissions they are likely to require in their manifest (a short file that describes the contents of the ‘package’). This allows the system to sandbox them from critical resources and gives the user some indication of what havoc they might reap. That’s the theory at least, but the first time I installed an application and read the permissions page I had no idea what they were on about! Clearly this system needs to be changed, but that is not what I want to talk about today.
As an application writer I need to know the protection level of these permissions, i.e. which of these permissions are normal (can cause the user no real harm), dangerous (might require a greater level of trust, such as the ability to read SMS messages), signature (only granted to applications that are signed by the people who built the OS), signatureOrSystem (like signature, but also allowed if they have been pre-installed in a system folder). I was surprised to find no easy reference for this in the documentation, but I did find the relevant information in the source.
You can of course probe the android package itself for this information, which is useful if you don’t have access to the particular version of Android you are running. Here is some code that does just that:
// Get the permissions for the core android package
PackageInfo packageInfo = getPackageManager().getPackageInfo("android", PackageManager.GET_PERMISSIONS);
if (packageInfo.permissions != null) {
// For each defined permission
for (PermissionInfo permission : packageInfo.permissions) {
// Dump permission info
String protectionLevel;
switch(permission.protectionLevel) {
case PermissionInfo.PROTECTION_NORMAL : protectionLevel = "normal"; break;
case PermissionInfo.PROTECTION_DANGEROUS : protectionLevel = "dangerous"; break;
case PermissionInfo.PROTECTION_SIGNATURE : protectionLevel = "signature"; break;
case PermissionInfo.PROTECTION_SIGNATURE_OR_SYSTEM : protectionLevel = "signatureOrSystem"; break;
default : protectionLevel = ""; break;
}
Log.i("PermissionCheck", permission.name + " " + protectionLevel);
}
}
…and here are the results in case you need to know them at a glance…
(more…)
1.0.41
adb CLI Client for ADB (Android Debug Bridge) Server.
adb [GLOBAL_OPTIONS] command [COMMAND_OPTIONS]
Connects to the ADB Server via its smart socket interface. Allows sending requests, receives responses and manages lifecycle of the adb server.
Tasks are performed via commands. Some commands are fulfilled directly by the server while others are “forwarded over to the adbd(ADB daemon) running on the device.
-a Listen on all network interfaces, not just localhost.
-d Use USB device (error if multiple devices connected).
-e Use TCP/IP device (error if multiple TCP/IP devices available).
-s SERIAL Use device with given SERIAL (overrides $ANDROID_SERIAL).
-t ID Use device with given transport ID.
-H Name of adb server host [default=localhost].
-P *PORT Smart socket PORT of adb server [default=5037].
-L SOCKET Listen on given socket for adb server [default=tcp:localhost:5037].
–one-device SERIAL|USB Server will only connect to one USB device, specified by a SERIAL number or USB device address (only with ‘start-server’ or ‘server nodaemon’).
–exit-on-write-error Exit if stdout is closed.
devices [-l] List connected devices.
-l Use long output.
help Show this help message.
version Show version number.
connect HOST[:PORT] Connect to a device via TCP/IP [default PORT=5555].
disconnect [HOST[:PORT]] Disconnect from given TCP/IP device [default PORT=5555], or all.
pair HOST[:PORT] [PAIRING_CODE] Pair with a device for secure TCP/IP communication.
forward –list | [–no-rebind] LOCAL_REMOTE | –remove LOCAL | –remove-all
–list List all forward socket connections.
[–no-rebind] LOCAL_REMOTE Forward socket connection using one of the followings.
tcp:PORT (local may be “tcp:0” to pick any open port. localreserved:UNIX_DOMAIN_SOCKET_NAME. localfilesystem:UNIX_DOMAIN_SOCKET_NAME. jdwp:PROCESS PID (remote only). vsock:CID:PORT (remote only). acceptfd:FD (listen only). dev:DEVICE_NAME. dev-raw:DEVICE_NAME. (open device in raw mode)**.
–remove LOCAL Remove specific forward socket connection.
–remove-all Remove all forward socket connections.
reverse –list | [–no-rebind] REMOTE LOCAL | –remove REMOTE | –remove-all
–list List all reverse socket connections from device.
[–no-rebind] REMOTE LOCAL Reverse socket connection using one of the following.
tcp:PORT (REMOTE may be “tcp:0” to pick any open port). localabstract:UNIX_DOMAIN_SOCKET_NAME. localreserved:UNIX_DOMAIN_SOCKET_NAME. localfilesystem:UNIX_DOMAIN_SOCKET_NAME.
–remove REMOTE Remove specific reverse socket connection.
–remove-all Remove all reverse socket connections from device.
mdns check | services Perform mDNS subcommands.
check Check if mdns discovery is available.
services List all discovered services.
push [–sync] [-z ALGORITHM] [-Z] LOCAL… REMOTE Copy local files/directories to device.
–sync Only push files that are newer on the host than the device.
-n Dry run, push files to device without storing to the filesystem.
-z enable compression with a specified algorithm (any/none/brotli/lz4/zstd).
-Z Disable compression.
pull [-a] [-z ALGORITHM] [-Z] REMOTE… LOCAL Copy files/dirs from device
-a preserve file timestamp and mode.
-z enable compression with a specified algorithm (any/none/brotli/lz4/zstd)
-Z disable compression
sync [-l] [-z ALGORITHM] [-Z] [all|data|odm|oem|product|system|system_ext|vendor] Sync a local build from $ANDROID_PRODUCT_OUT to the device (default all)
-n Dry run. Push files to device without storing to the filesystem.
-l List files that would be copied, but don’t copy them.
-z Enable compression with a specified algorithm (any/none/brotli/lz4/zstd)
-Z Disable compression.
shell [-e ESCAPE] [-n] [-Tt] [-x] [COMMAND…] Run remote shell command (interactive shell if no command given).
-e Choose escape character, or “none”; default ‘~’.
-n Don’t read from stdin.
-T: Disable pty allocation.
-t: Allocate a pty if on a tty (-tt: force pty allocation).
-x Disable remote exit codes and stdout/stderr separation.
emu COMMAND Run emulator console COMMAND
(see also adb shell cmd package help):
install [-lrtsdg] [–instant] PACKAGE Push a single package to the device and install it
install-multiple [-lrtsdpg] [–instant] PACKAGE… Push multiple APKs to the device for a single package and install them
install-multi-package [-lrtsdpg] [–instant] PACKAGE… Push one or more packages to the device and install them atomically
-r: Replace existing application.
-t Allow test packages.
-d Allow version code downgrade (debuggable packages only).
-p Partial application install (install-multiple only).
-g Grant all runtime permissions.
–abi ABI Override platform’s default ABI.
–instant Cause the app to be installed as an ephemeral install app.
–no-streaming Always push APK to device and invoke Package Manager as separate steps.
–streaming Force streaming APK directly into Package Manager.
–fastdeploy Use fast deploy.
-no-fastdeploy Prevent use of fast deploy.
-force-agent Force update of deployment agent when using fast deploy.
-date-check-agent Update deployment agent when local version is newer and using fast deploy.
–version-check-agent Update deployment agent when local version has different version code and using fast deploy.
–local-agent Locate agent files from local source build (instead of SDK location). See also adb shell pm help for more options.
uninstall [-k] APPLICATION_ID Remove this APPLICATION_ID from the device.
-k Keep the data and cache directories.
bugreport [PATH] Write bugreport to given PATH [default=bugreport.zip]; if PATH is a directory, the bug report is saved in that directory. devices that don’t support zipped bug reports output to stdout.
jdwp List pids of processes hosting a JDWP transport.
logcat Show device log (logcat –help for more).
disable-verity Disable dm-verity checking on userdebug builds.
enable-verity Re-enable dm-verity checking on userdebug builds.
keygen FILE Generate adb public/private key; private key stored in FILE.
wait-for [-TRANSPORT] –STATE… Wait for device to be in a given state.
STATE: device, recovery, rescue, sideload, bootloader, or disconnect. TRANSPORT: usb, local, or any [default=any].
get-state Print offline | bootloader | device.
get-serialno Print SERIAL_NUMBER.
get-devpath Print DEVICE_PATH.
remount [-R] Remount partitions read-write.
-R Automatically reboot the device.
reboot [bootloader|recovery|sideload|sideload-auto-reboot] Reboot the device; defaults to booting system image but supports bootloader and recovery too.
sideload Reboots into recovery and automatically starts sideload mode.
sideload-auto-reboot Same as sideload but reboots after sideloading.
sideload OTAPACKAGE Sideload the given full OTA package OTAPACKAGE.
root Restart adbd with root permissions.
unroot Restart adbd without root permissions.
usb Restart adbd listening on USB.
tcpip PORT Restart adbd listening on TCP on PORT.
start-server Ensure that there is a server running.
kill-server Kill the server if it is running.
reconnect Close connection from host side to force reconnect.
reconnect device Close connection from device side to force reconnect.
reconnect offline Reset offline/unauthorized devices to force reconnect.
Only valid when running with libusb backend.
attach SERIAL Attach a detached USB device identified by its SERIAL number.
detach SERIAL Detach from a USB device identified by its SERIAL to allow use by other processes.
host-features
list features supported by adb server.
features
list features supported by both adb server and device.
$ADB_TRACE Comma (or space) separated list of debug info to log: all,adb,sockets,packets,rwx,usb,sync,sysdeps,transport,jdwp,services,auth,fdevent,shell,incremental.
$ADB_VENDOR_KEYS Colon-separated list of keys (files or directories).
$ANDROID_SERIAL Serial number to connect to (see -s).
$ANDROID_LOG_TAGS Tags to be used by logcat (see logcat –help).
$ADB_LOCAL_TRANSPORT_MAX_PORT Max emulator scan port (default 5585, 16 emulators).
$ADB_MDNS_AUTO_CONNECT Comma-separated list of mdns services to allow auto-connect (default adb-tls-connect).
$ADB_MDNS_OPENSCREEN The default mDNS-SD backend is Bonjour (mdnsResponder). For machines where Bonjour is not installed, adb can spawn its own, embedded, mDNS-SD back end, openscreen. If set to “1”, this env variable forces mDNS backend to openscreen.
$ADB_LIBUSB ADB has its own USB backend implementation but can also employ libusb. use adb devices -l (usb: prefix is omitted for libusb) or adb host-features (look for libusb in the output list) to identify which is in use. To override the default for your OS, set ADB_LIBUSB to “1” to enable libusb, or “0” to enable the ADB backend implementation.
Automated Installation Kit (AIK) for Windows 7 32bit
! NOTE To install the Windows AIK, you must first download the ISO, Write the ISO file to a DVD using a third party tool, and then install the Windows AIK from the DVD.
All Permissions on Android 14
Here are all the 880 Android permissions that exist in Android 14. The permissions marked with asterisks (*) are only granted to system apps.
(more…)
![]()
Some browser hidden options:
internet://debug/
List of Internet URLs
internet://attribution-internals
internet://autofill-internals
internet://bluetooth-internals
internet://credits
internet://dns
internet://flags
internet://gpu
internet://interstitials
internet://media-internals
internet://net-export
internet://net-internals
internet://newtab
internet://newtabcontent
internet://parental-control
internet://password-manager-internals
internet://serviceworker-internals
internet://tracking
internet://version
internet://webapks
(more…)
Take ownership of file or folder
In windows, some of the system files are protected by OS and can’t be accessed by users with even administrator privileges. CSC cache stored in C:\Windows\CSC is one such folder. If you try to open the folder in windows explorer, you would be greeted with the window ‘You don’t currently have permission to access this folder. Click Continue to permanently get access to this folder.”
Take ownership of a file/folder from windows command line?
Open elevated administrator command prompt and run the below command on the file.
takeown /F fileName
Running from a non elevated command prompt would generated the error ‘Access is denied’
Take ownership of a folder and all its contents:
c:>takeown /R /F c:\windows\csc\
SUCCESS: The file (or folder): “c:\windows\csc\” now owned by user “domain\user”.
These commands work on Windows 8 and Windows 7.