How to fix my Windows Blue Screen
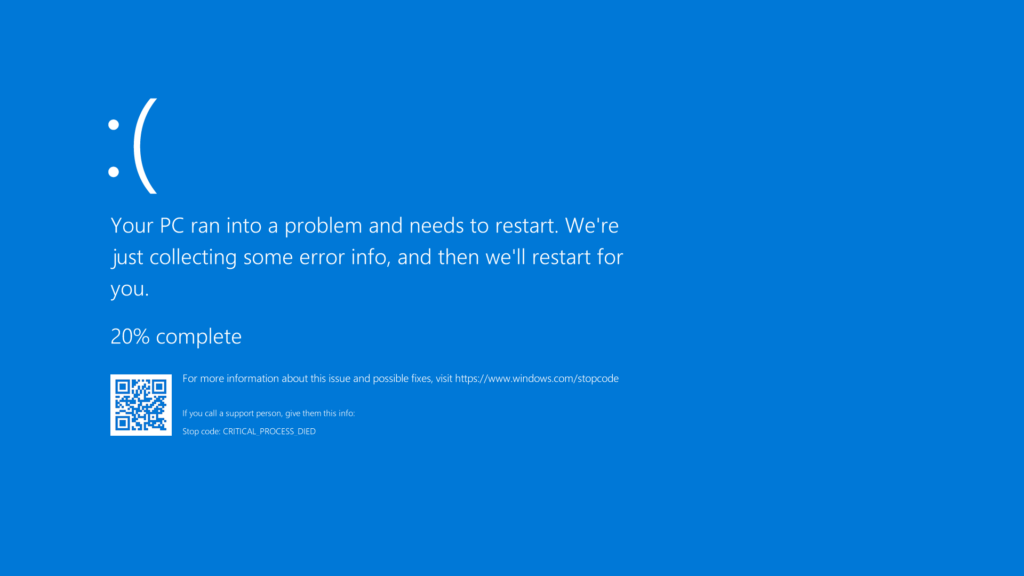
If you have CrowdStrike on your computer, and it’s suffering from a BSOD, several system admins on a Reddit thread have shared a potential fix. You’ll need to boot Windows into Safe Mode or the Windows Recovery Environment and delete a file. If you know how to get into Safe Mode quickly on your computer, skip the first nine steps, which are from Microsoft, and go straight to the last two, which are from CrowdStrike:

